Microsoft Cloud App Security Log Collector Troubleshooting

Copy the contents of the screen because you will need the information when you configure the log collector to communicate with cloud app security.
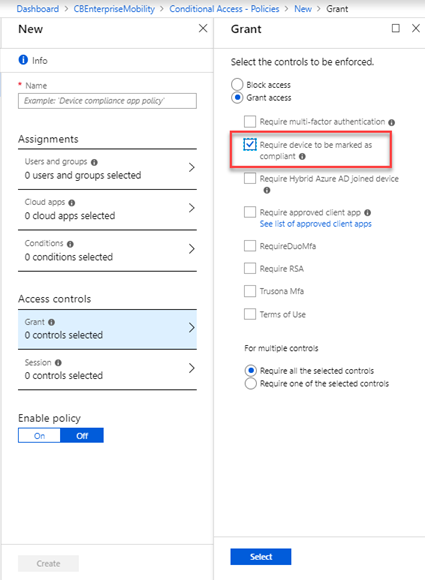
Microsoft cloud app security log collector troubleshooting. If you work with both cloud app security and zscaler you can integrate the two products to enhance your security cloud discovery experience. Troubleshooting microsoft cloud app security status. Most popular data sources are already supported. For tenant activation support see ways to contact support for business products admin help.
After you have a license for cloud app security you ll receive an email with activation information and a link to the cloud app security portal. The 151 return on investment roi the net present value. If you selected syslog this information will include information about which port the syslog listener is listening on. Log collectors enable you to easily automate log upload from your network.
Copy the contents of the screen because you will use it when you configure the log collector to communicate with cloud app security. Define data sources and link them to a log collector. Your organization must have a license to use cloud app security. Step 1 web portal configuration.
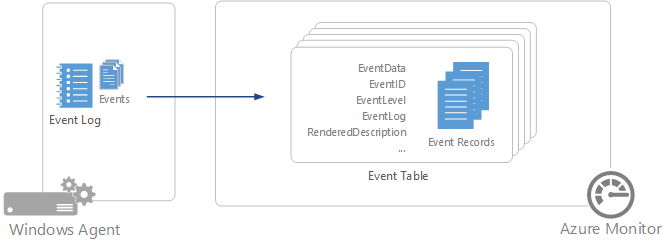
Ftp logs are uploaded to microsoft cloud app security after the file finished the ftp transfer to the log collector. The log collector runs on your network and receives logs over syslog or ftp. A single log collector can handle multiple data sources. For each firewall or proxy from which you want to upload logs create a matching data source.
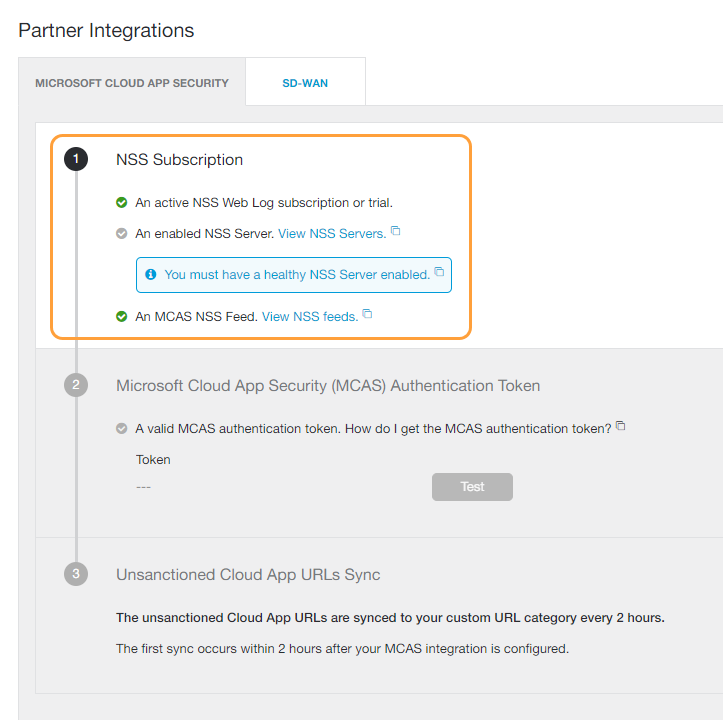
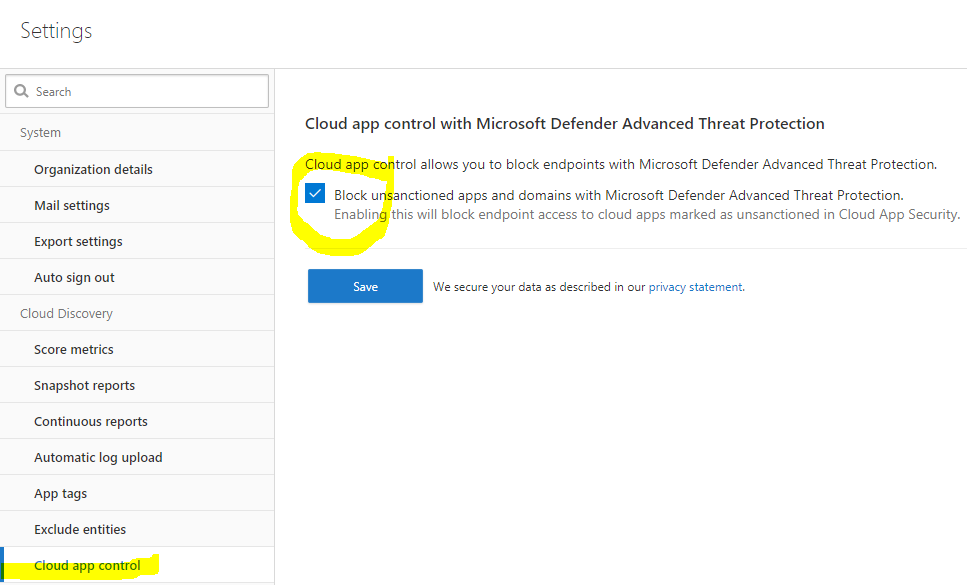
The infographic shows a bar chart at left stacking the benefits of deploying microsoft cloud app security. Check the current status of microsoft cloud app security. Stay up to date with our blog. In the cloud app security portal click the settings icon followed by log collectors.
Each upload of an unsupported data source is reviewed and added to the pipeline for new data source parsers. Go to the automatic log upload settings page. On the help support page you can view the list of recent support requests and select them to view additional details. Each log is automatically processed compressed and transmitted to the portal.
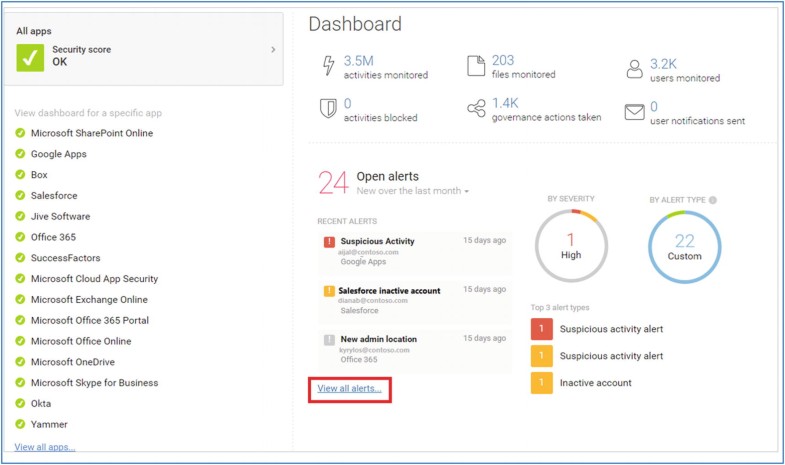
Talk to a community of peers. Start a trial today. On the right there are three important numbers noted. The cloud app security technical team builds a dedicated parser per each data source.
Instead it s sent for review to the cloud app security technical team. Click add data source. We would like to show you a description here but the site won t allow us. From lowered time and effort for remediation of incidents to improved compliance and auditing the savings total over 8 9m.
The log collector runs on your network and receives logs over syslog or ftp. For syslog the log collector writes the received logs to the disk.